By TOM BOWSER
Pro Tools is set to use pre-fader metering by default. You know Pro Tools is set to pre-fader metering if you move a volume fader up or down and the level shown by the meter does not change.
To set either pre or post fader metering:
- Left click on "Options" on the Pro Tools menu bar.
- If "Pre-Fader Metering" has a checkmark to the left then pre fader metering is being used in the session. See the image below.
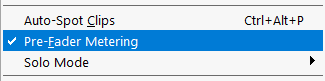
- If there is no checkmark then "Post-Fader Metering" is used in the session.
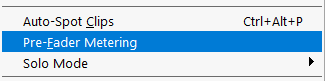
Pre (before) Fader Metering: The meter shows the level of the audio signal BEFORE it passes the volume fader. If you move the volume fader up or down the signal level the meter displays will remain the same.
Post Fader Metering: The meter shows the audio signal after it has passed through plug-ins inserted on the track and after the volume fader.
If you move the volume fader higher the signal level the meter displays will increase. If you move the volume fader lower the signal level the meter displays will decrease.
Typically, pre-fader metering is used during recording to set levels coming into your DAW and post fader metering is used when mixing.
Whether you use pre or post fader metering while mixing is a matter of preference. I like to view a new mix using pre-fader metering to verify that all track levels are where I expect them to be, no signal is too high or low.
Generally, once I begin to mix a session I switch to post fader metering for the rest of the time I spend mixing.